russian hackers and military work in “tandem”
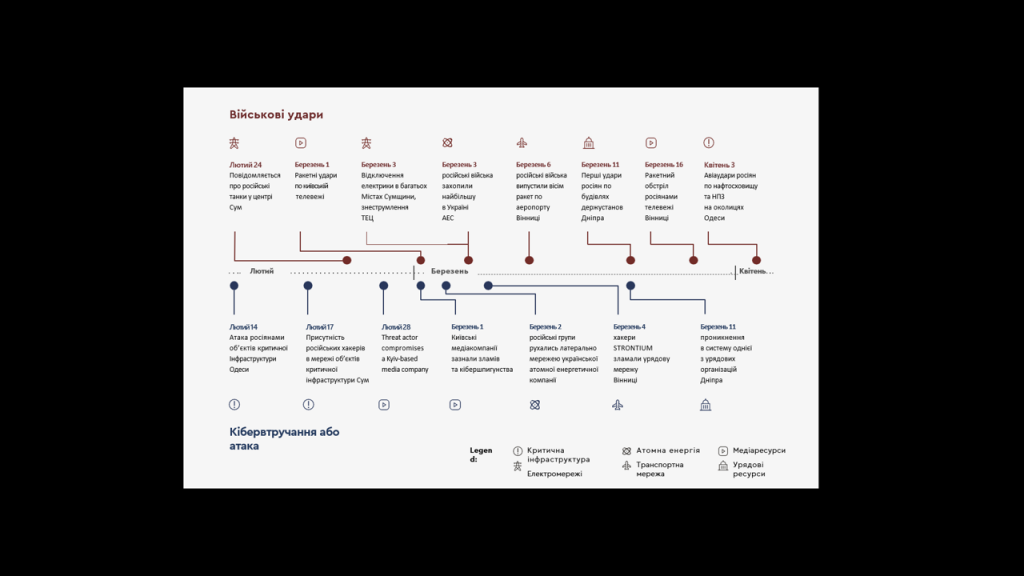
Cyberattacks against Ukraine have been used strategically to support ground campaigns, with state-sponsored advanced persistent threat (APT) groups behind attacks that began in February.
Microsoft researchers believe six separate russia-aligned threat actors carried out 237 cyber operations tied with ground campaigns, that resulted in threats to civilian welfare and attempted to carry out dozens of cyberespionage attacks against Ukrainian targets.
Microsoft has released an in-depth report detailing how russian cyberattacks against Ukraine were “strongly correlated” or “directly timed” with its military operations in the country.
Researchers disclosed that russian hackers and military worked in “tandem” to launch relentless cyberattacks on Ukraine since the war began on February 24. Some security breaches were also reportedly carried out about a year before the massive hit on the east European geopolitics landscape.
For example, on March 1, several Kyiv-based media companies were struck by destructive and information-stealing malware, which coincided with a missile strike on a Kyiv TV tower on the same day.

Russia is believed to be using cyberattacks in a type of “hybrid war”, according to a blog post by Tom Burt, corporate vice president of Customer Security and Trust at Microsoft. He claimed that russia’s use of cyber strikes “appear to strongly correlated and sometimes directly timed” with the “kinetic” military operations on services and institutions in Ukraine. “The attacks have not only degraded the systems of institutions in Ukraine but have also sought to disrupt people’s access to reliable information and critical life services on which civilians depend, and have attempted to shake confidence in the country’s leadership,” Burt said.
‘Hybrid’ War
Microsoft security teams have been working closely with Ukrainian government officials as well as both government and private-enterprise cybersecurity staff to identify and remediate threat activity against Ukrainian networks, researchers said.
russia appears to have been preparing for the land conflict with Ukraine in cyberspace about a year before the war began, or since March 2021, according to the report.
In the lead up to the ground conflict and the subsequent invasion, threat groups with known or suspected ties russia “continuously developed and used destructive wiper malware or similarly destructive tools on targeted Ukrainian networks at a pace of two to three incidents a week,” researchers found.
“From February 23 to April 8, we saw evidence of nearly 40 discrete destructive attacks that permanently destroyed files in hundreds of systems across dozens of organizations in Ukraine,” they wrote.
Even before that, in January, Microsoft identified a Master Boot Record (MBR) wiper attack that it named WhisperGate targeting Ukraine to permanently disrupt organizations across the country and paint it as a failed state. Wipers are the most destructive of malware types because they permanently delete and destroy data and/or systems, causing great financial and reputational damage to victims.
From late February to mid-March, another series of wiper attacks using malware called HermeticWiper, IsaacWiper and CaddyWiper targeted organizations in the Ukraine as russia commenced its physical invasion.
Source: Microsoft