Financial companies and wealthy people used to be the target for scammers and criminals. The capitalization of cryptocurrency market of hundreds of billions of dollars has become the spotlight for cybercriminals of all hues. The same stays for ICO.
The main driver of cybercrime in the cryptocurrency market is that transactions are irreversible.
Even by immediately fixing an illegitimate transaction, the owner of cryptocurrency will not be able to appeal to arbitrage and block it as with FIAT currencies (there are cases of using a hard fork to roll back transactions, block stolen tokens, etc. However, all this is entirely at odds with the concept of the financial system on the blockchain and is the subject of heated disputes among crypto-anarchists).
How to take part in promising (or not so) ICOs and avoid becoming a victim of cyber fraud? In order to minimize most of the risks of stealing investment funds, it is necessary to follow simple rules of digital (or cyber) hygiene.
Before considering the list with rules, look at the ways of stealing investment funds. There are basically two approaches – technical and social engineering (the psychological manipulation of people into performing actions or divulging confidential information.) We do not account for fraudulent ICOs in this list. Therefore, we offer the tips to cover these two approaches:
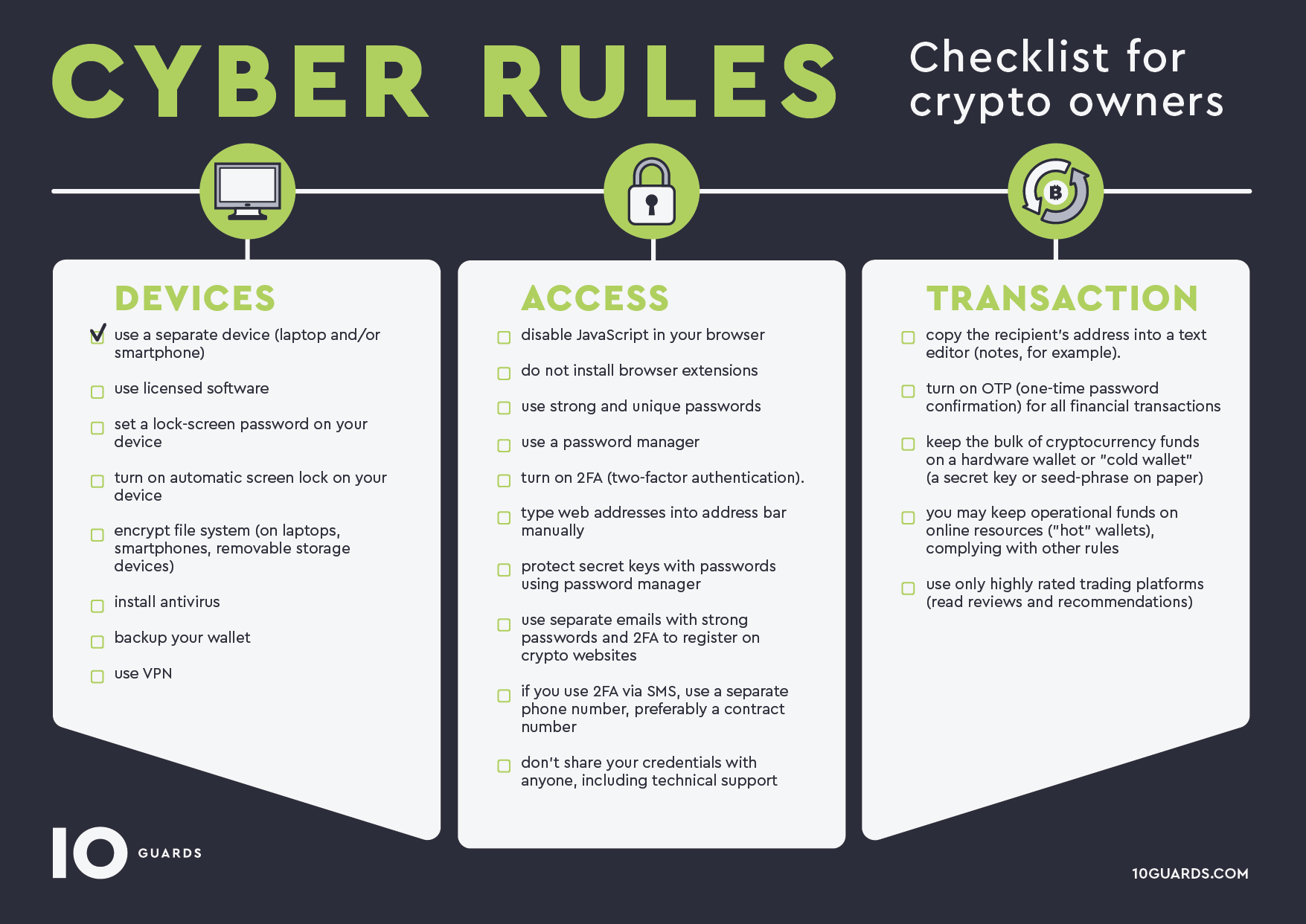
1. Technically, cybercriminals can gain access to any of your devices: computer, laptop, smartphone, tablet, and redirect you instead of the ICO project website to its fake copy. As a result, you will transfer crypto funds not to your wallet, but to the fake wallet of scammers. Also, when accessing your devices, “black” hackers can hack your crypto wallets grabbing your private keys and/or passwords, as well as spoof wallet addresses for recipients during transactions. How to protect yourself?
- Be sure to install the latest OS updates, patches, firmware, and all available programs. Software and hardware updates often include software patches. They cover the security holes to keep hackers out.
- Use where possible two-factor authentication (2FA) to access hot crypto wallets and/or ICO platforms. It is recommended to avoid using SMS, but if you chose SMS, then sign up a contract with a mobile operator to make it difficult to restore your SIM card without you. In a perfect world use special software or hardware products for the second factor.
- Install security software (antivirus, firewall, sandboxes, etc.). As mentioned above, most mass attacks are carried out using already known “viruses” and antivirus software can protect against them.
- On your device for working with cryptocurrency transactions, install the minimum number of third-party applications, browser extensions, etc. Reduce the risk of installing software with built-in backdoors, as well as vulnerabilities that would allow remote unauthorized access to your device.
- Do not use public Wi-Fi networks for cryptocurrency transactions, or make sure that you use a VPN connection.
- Try to always use a VPN connection, not so much to remain anonymous, but to encrypt connections and protect against interception of traffic by cyber intruders.
2. Using social engineering, cyber fraudsters provoke you to take rash steps – to follow a fake link, to go to a fake project website, to launch a malicious file on your device, etc. For protection, follow these rules:
- Double-check the web address (URL) in the address bar to make sure you’re going to the right webpage, or rather do not follow the link but enter your address manually (you can add the correct link to your bookmarks and open the project website from the bookmarks).
- Check the address of the crypto wallet to which you are sending cryptocurrency.
- Installing some programs, download the installer from the official website, and verify the checksum of the file. Do not install programs received by mail, through messengers, or from unofficial sites.
- Do not share private keys from crypto wallets with large amounts. Moreover, keep a separate wallet with minimum amounts at the crypto exchange. Also, do not share your passwords from hot wallets and never reuse passwords from important accounts.
The team that launches the ICO should take on responsibility for the investors’ security. Here are the least they must do:
- run an independent assessment of the IT infrastructure security level (internal and external) and web applications;
- run an independent smart contract security audit;
- enable two-factor authorization for their investors to access their financial information and crypto wallets;
- track the phishing resources with names similar to their project,
Detecting and tracking phishing campaigns through web analytics identifiers: project mentions on the Internet, messengers, and, ideally, the darknet. Promptly block phishing domains and respond to fraudulent mentions of your project;
- track suspicious activity within your IT infrastructure;
- build cybersecurity processes within the project team and remember that a secure project always costs more.
Here are some cyber rules that you should follow: