Information security and cybersecurity share the same goals of protecting people, data, and devices. The difference between the two areas is the approach and scope of protection.
Information security (InfoSec)
Information security refers to protecting data from accidental or intentional interference. The methods are grouped into technical, administrative, legal, and physical.
Technical protections include firewalls, anti-virus software, authentication, and encryption systems. It is also important to properly regulate access to facilities for groups and each participant. For this purpose, the principle of information accessibility is respected.
Administrative-legal protection means the introduction of a set of rules for the use of data and infrastructure. Legal methods also include licensing of security activities and certification of information objects.
Physical protection measures include security facilities, locks, safes, and surveillance cameras.
To secure resources in the enterprise, comprehensive audits must be conducted regularly, and policies must be implemented in accordance with international standards for data protection and management (e.g., ISO 27001). Evaluation and implementation can be the responsibility of either internal security managers or an external team.
Cybersecurity
Cybersecurity protects against cyberattacks that aim to breach information security (i.e., prevent hackers from gaining digital access to data in networks, computers, and programs). It requires regular vulnerability scanning and penetration testing.
Compliance with cybersecurity and IT security requirements is part of InfoSec’s enterprise policy. Otherwise, basic information requirements (confidentiality, integrity, and availability) will not be met.
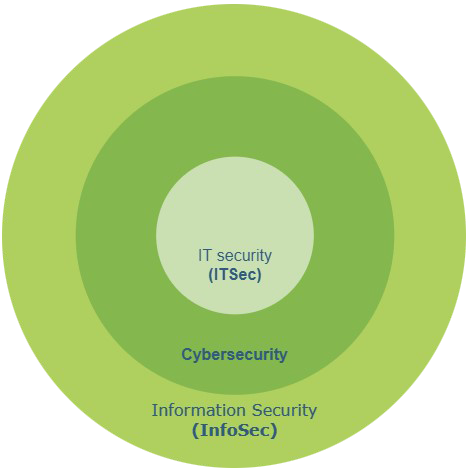
Thus, information security is an industry that covers a wide range of information security and related issues.