When did you last update your passcodes? Cybersecurity experts say 95% of cyber-attacks are due to human error.
Nowadays, everything requires a login and passcode. There is nothing new to say that there are people on the Internet who are willing to find out any kind of passwords. Of course, you don’t have much to worry about unless you are a high-ranking politician or celebrity, but it never hurts to have good protection. No matter how strong you make it, it’s still at risk for hackers to get into it.
Maintaining good password hygiene is important. But unless you use a password manager, remembering all of them is a miserable experience.
Your password can be exposed in seconds.
When you create a new account on a website or service it is essential to pay attention to the indications that they tell you with the passwords. Many sites give you certain bits of advice on how to improve the protection of your password and all thanks to the use of special characters and numbers. This is key to have a strong password, otherwise, a hacker can steal your account in seconds.
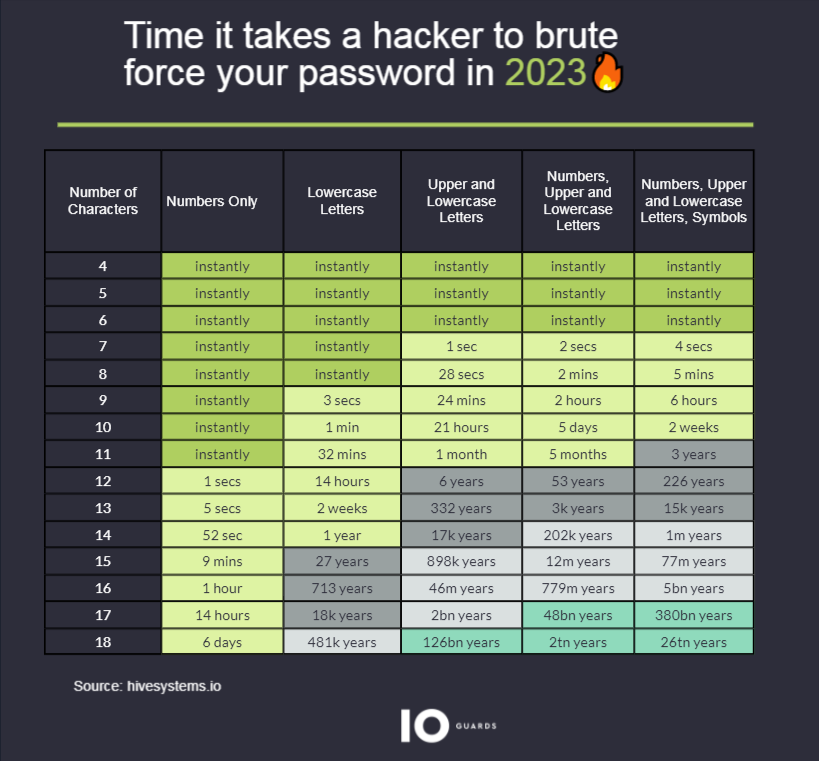
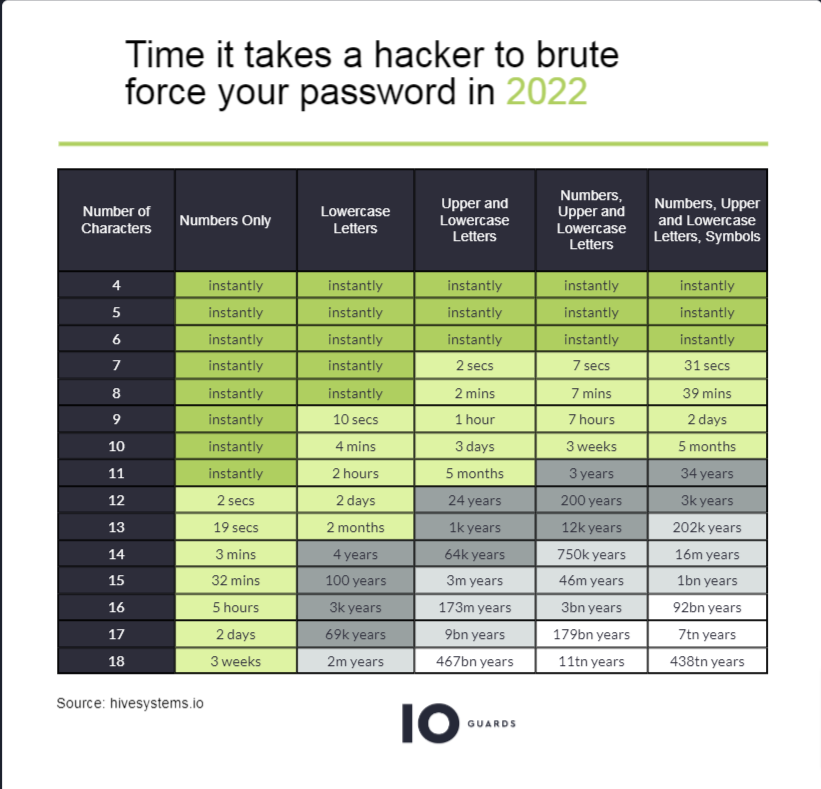
The cybersecurity company Hive Systems just released its 2023 password table that describes how easy it can be for hackers to break into your accounts (see also the table of 2022.)
In 2020, a simple eight-character passcode would take hours to crack. Three years later, they’re doing it in five minutes.
“We see the times implicit able in 2020 get halved and sometimes even more here in 2023,” said Alex Nette, the CEO, and co-founder of Hive Systems, “That shows the rapid pace of computing power that’s being developed and that’s one part of the problem.”
The second part of the problem is how those websites and companies store and encrypt your passwords.
“So as the computing power goes up, the encryption is still staying the same. That’s a huge problem,” said Nette. ”There are better encryption methods available that websites can use, they’re just not using it, and that’s why we as consumers have to take this power back in our hands and set those solid and secure passwords ourselves.”
Using ChatGPT hardware has also played a role in hackers’ ability to brute force your account.
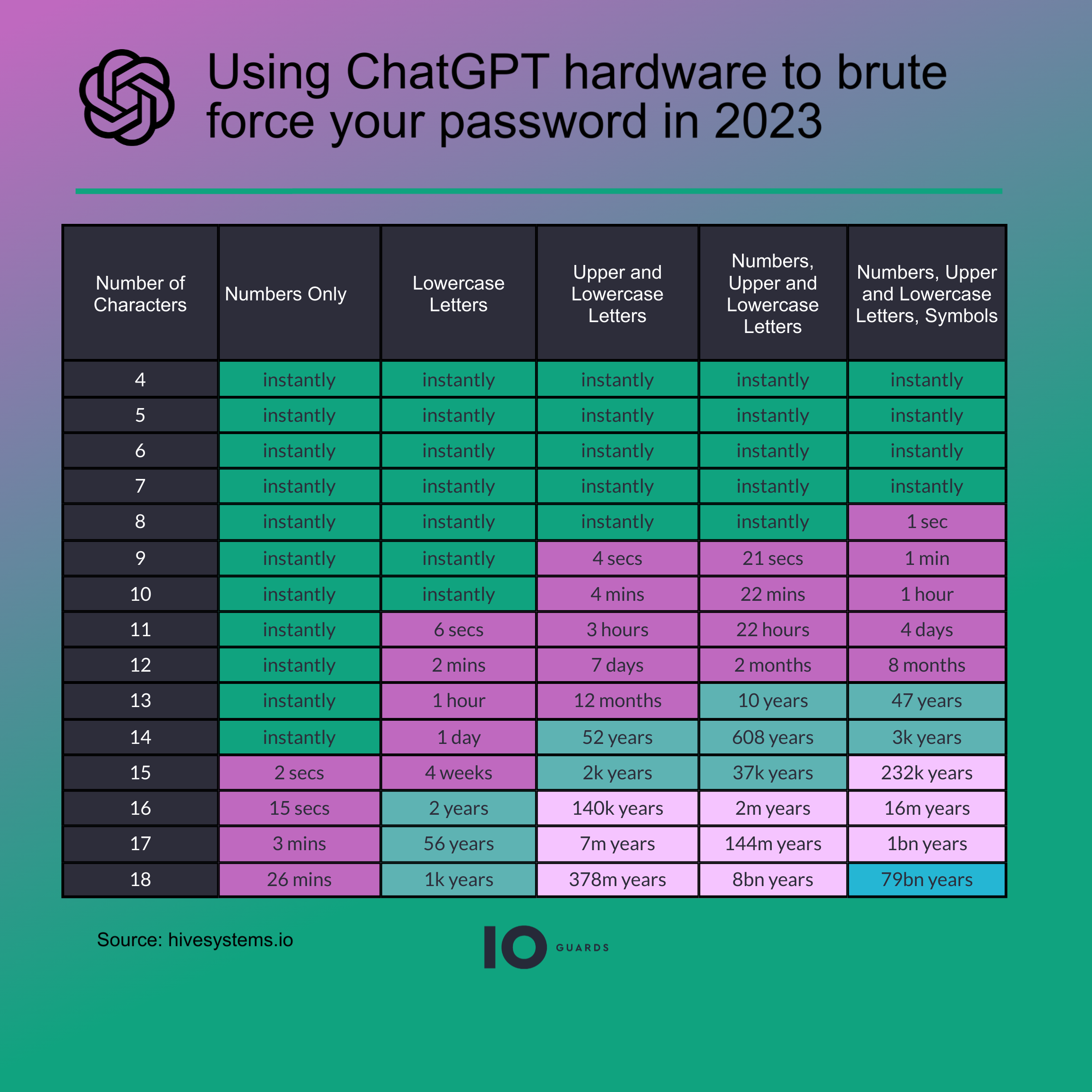
“The biggest vulnerability and risk to you as a person is reusing passwords or using some sort of passcode methodology,’ said Alex Nette.
According to Nette, if you see your password here and say that time is only two weeks, that is the worst-case scenario for a hacker. With more money and computing power over time, these times have slowed down. This means that passwords may be hackable instantaneously next year.
“So take the time to protect yourself, go through and identify and inventory all of your online accounts and make sure they are secure,” Nette said.
Source: hivesystems.io




