The explosive growth in the quantity and quality of personal data in the last decade has stimulated new opportunities in economic and social fields. But there are two sides to every story. The irresponsible approach to the collection, processing, storage, and distribution of personal information has led to many leaks and, consequently, to its illegal use. Often we do not even realize how much personal data about each of us is collected and stored.
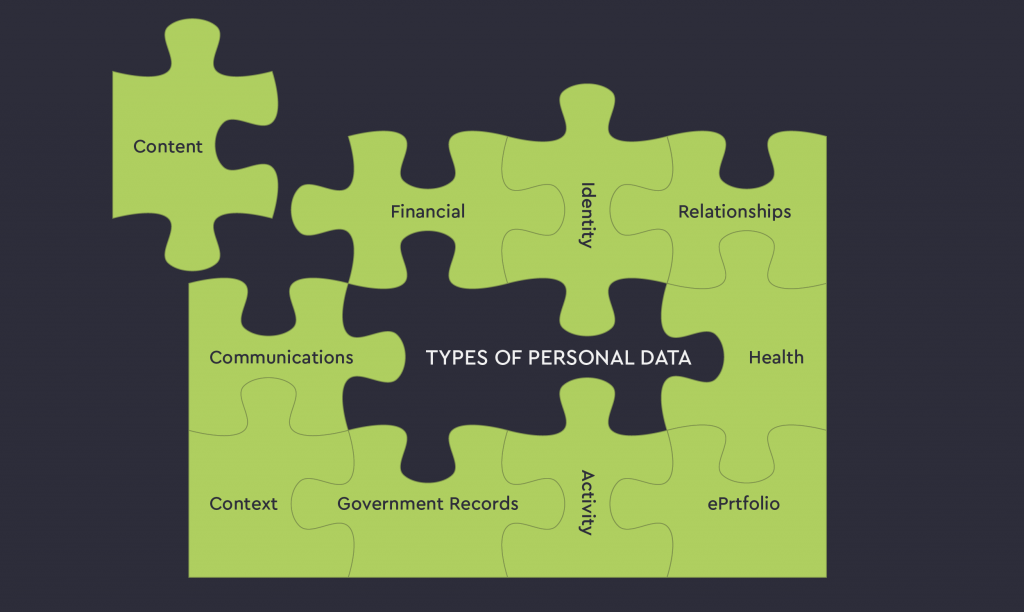
TYPES OF PERSONAL DATA
- Identity
- Financial
- Government Records
- Health
- Content
- ePortfolio
- Communications
- Relationships
- Context
- Activity
Identity:
- Identifiers:
- Usernames
- Emails
- Phone Numbers
- Nicknames
- Personas
- Personal Devices
- Device IP
- IP Addresses
- Bluetooth IDs
- SSIDs
- SIMs
- IMEIs
- Demographic Data:
- Age
- Sex
- Addresses
- Education
- Work History
- Resume
- Declared Interests:
- Likes
- Favorites
- Preferences
- Settings
Financial:
- Financial
- Incomes
- Expenses
- Transactions
- Taxes
- Assets
- Accounts
- Liabilities
- Insurance
- Credit Rating
- Corporations
- Goods:
- Virtual
- Digital Records of Physical
Government Records:
- Legal Names
- Life Events:
- Records of Birth
- Marriage
- Divorce
- Death
- Law Enforcement
- Military Service
Health:
- Care
- Insurance
Content:
- Private Documents
- Consumed Media:
- Books
- Photos
- Videos
- Music
- Podcasts
- Produced Music
- Software
ePortflio:
- Academic
- Employment
Communications:
- Text
- IM/SMS
- Posts
- Shared Texts
- Shared Bookmarks and Links
- Speech
- Social Media Consumed:
- Photos
- Videos
- Streamed Videos
- Podcasts
- Software
- Produced Music
- Presence
Relationships:
- Address book Contacts
- Communications Contacts
- Social Network Links
- Family and Genealogy
- Group Memberships
- Call and Message Logs
Context:
- Location:
- Current
- Past
- Planned
- People
- Objects
- Events:
- Calendar Data
- Event Data from Web Services
Activity:
- Real World:
- Eating
- Driving
- Sleeping
- Shopping
- Client Applications and OS
- Browsed
Source: Rethinking Personal Data Pre-Read Document