2020 is a real game-changer – an epidemic, unemployment, a new way of life, and mass transition to online – that is what 2020 brought us. While we all continue to adapt to the new reality and think about the future, cybercriminals seem to take to it like a duck to water. Only in May, the number of leaks almost reached 9 billion records.
Today we will talk about the largest DDoS attacks in the first six months of 2020 and about companies that hackers have shifted their focus to during the pandemic.
The Denial of Service (DDoS) attack aims to disable a website by sending thousands of requests per second to overload the website server and cause it to fail.
DDoS attacks increased by 542% between the fourth quarter of 2019 and the first quarter of 2020. Their number doubled in the second quarter. At the same time, the number of small attacks continues to increase, while large attacks are becoming more and more widespread. Vivek Ganti and Omer Yoachimik wrote about this on the Cloudflare blog.
Moreover, the authors claim that the second quarter recorded the largest DDoS attacks ever.
As for duration, 83% of all attacks lasted from 30 to 60 minutes. A similar trend observed in the first quarter: 79% of attacks had the same range.
These may not seem significant, but imagine that this is a cyber-battle lasting 30 to 60 minutes between your cybersecurity team and the hacker. Now the attack doesn’t look so painless and short.
Besides, if even a short DDoS attack causes a failure or deterioration in system maintenance, you can spend a lot of time restoring, rebooting your devices, and restarting services. At the same time, you lose income and reputation every minute.
POETIC JUSTICE
The American company Cloudflare, which provides CDN services, protection against DDoS attacks, as well as secure access to resources and DNS servers, has recently been attacked.
It all started on June 18 and lasted four days. At the peak, the DDoS-attack reached a speed of 754 million packets per second. Traffic forwarded from more than 316,000 different IP addresses to one Cloudflare IP address, which mainly used for sites that provide a free plan to customers.
The company said that the attackers tried (and failed) to overload routers and data center devices with high packet transfer rates (754 million / s).
If you visualize this attack, the packet stream is a swarm of millions of mosquitoes that need to be killed one by one.
Cloudflare claims to have been able to handle the incident without much trouble. According to some reports, this could have been a diversionary tactic from large-scale data theft or a test before future attacks.
Another company that provides Internet security services has caught in the crossfire of cybercriminals. On June 21, Akamai extinguished the largest DDoS attack of the PPS type (packet per second) previously recorded on the platform.
The cyberattack generated 809 million packets per second and targeted a major European bank. PPS attacks mainly designed to overload network equipment and systems in the data center or cloud infrastructure.
Unlike DDoS attacks, which disrupt Internet resources, they exhaust hardware resources. Curiously, the growth of source IP addresses was explosive – the cyberattack took off from ordinary traffic levels to 418 Gbps almost instantly. Then it reached a peak of 809 million packets per second in about two minutes.
Akamai notes that the vast majority of the attack traffic originated from unknown IP addresses, which indicates the emergence of a botnet. Before that, the record traffic volume of a PPs attack was only 293.1 million packets per second, which is 2.7 times less than the incident with Akamai.
Amazon AWS Shield also extinguished a 2.3 Tb/s DDoS attack.
We don’t know which client suffered from the cyberattack. The AWS Shield Threat Landscape Report only mentions that DDoS was organized using compromised CLDAP web servers. The attack lasted three days.
TIDBIT
As COVID-19 came into our lives, we began to use delivery services, educational platforms, game servers, remote communication platforms, and medical resources more often. No wonder that hackers have shifted their focus to these businesses.
Cybercriminals especially fascinated by the medical sector. In March, cybercriminals attempted to block the work of the U.S. Government Department of Health and Human Services (HHS), and the hospital network in Paris Assistance Publique – Hôpitaux de Paris (APHP), which consists of 44 institutions.
We recently wrote about the unhealthy love of hackers for the World Health Organization as well as for the hospitals and research centers that have suffered from cyberattacks.
Several European food delivery services experienced DDoS attacks. The German Takeaway.com (Lieferando.de) was attacked during the peak of orders on their website.
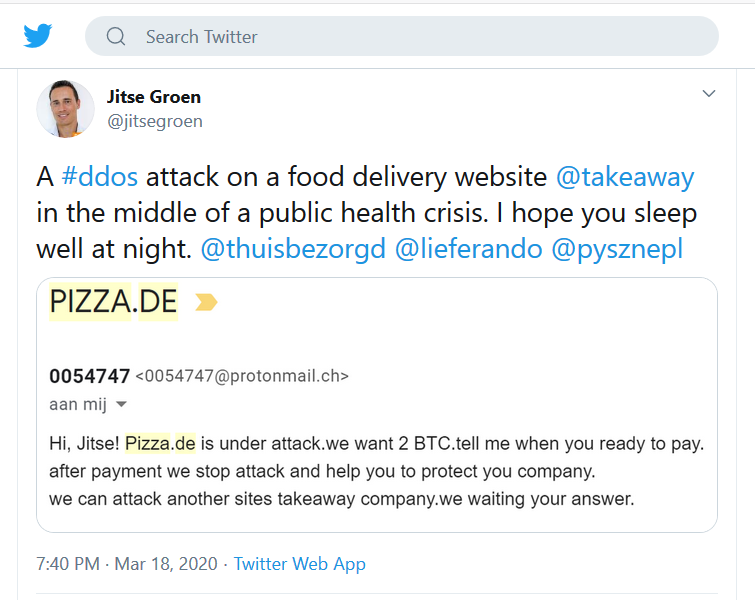
The company could take orders but not process them. Hackers demanded two bitcoins to stop the attack.
According to the CEO of the company, no one paid the ransom. This situation caused a lot of damage to Lieferando due to the size of its delivery network – more than 15 thousand restaurants in Germany.
The consequences affected customers, restaurant owners, and the reputation of the service. Lieferando had to compensate users for the orders they had paid for, but that failed to deliver.
A similar story happened to the Dutch delivery service Thuisbezorgd.
Cybercriminals also paid attention to the education platforms. In March, the German online platform Mebis was affected by a DDoS attack.
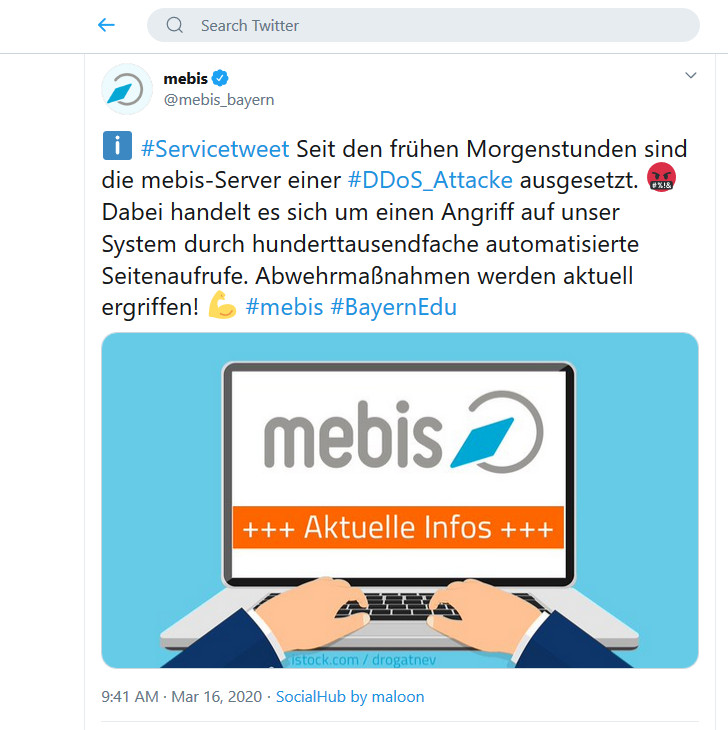
When the online classes started, the website was down for a couple of hours. Probably it was a joke of some Bavarian student, who wasn’t very enthusiastic about studying.
Those who liked to play had to get nervous too. The multiplayer game EVE Online was under the pressure of DDOS attack for nine days. Also, the gaming platform Blizzard had similar issues, and in January,
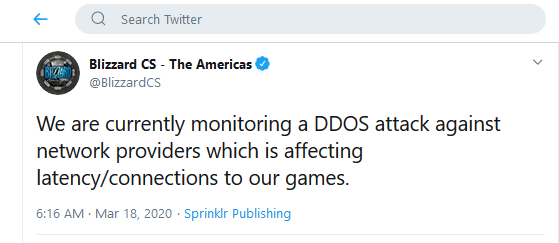
Wargaming servers were undergoing a prolonged DDoS attack too.
The servers of the government agencies were also affected.
For example, in Greece, the websites of ministries, emergency services, and even the police were out of order. The U.S. voter registration site was also affected by the attack. Hackers used the technique of pseudo-random attack on subdomains (PRSD), requests were made for at least one month with an interval of about two hours, the frequency reached a peak of about 200 thousand DNS-requests.
By the way, the largest DDoS attack known took place in February 2018. The target of this attack was GitHub – a popular online service for code management, which is used by millions of developers. At the peak of the attack was recorded incoming traffic at 1.3 terabytes per second (Tbps) and sending packets at 126.9 million per second.
Source: Хабр




